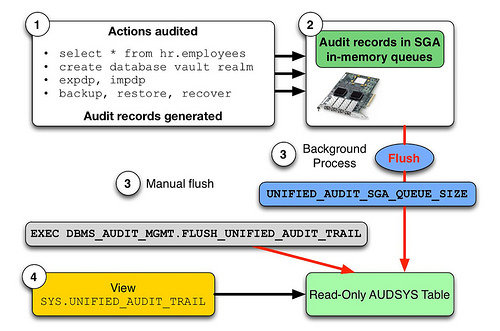
Unified Auditing is new audit feature came with Oracle 12c version. You have to do enable Unified Auditing to use after install database. Unified Auditing come as disabled by default. In previous releases of Oracle Database, there were separate audit trails for individual components: SYS.AUD$ for the database audit trail, SYS.FGA_LOG$ for fine-grained auditing, DVSYS.AUDIT_TRAIL$…
Category: Database Security
How to Change Oracle Enterprise Manager Port Number
If you want to change Oracle Enterprise Manager port number, you can use “emca -reconfig ports -DBCONTROL_HTTP_PORT ” command, this is simple. You can use to take security measure for Oracle EM. I will give 1820 as port for Oracle EM as example. Change Oracle Enterprise Manager Port
RMAN Encrypt Backup in Oracle
You can protect your backups with rman encryption. You have three ways to rman backup encryption. You can use wallet, password or dual mode. I will tell you password protection. Configure RMAN Backups With Password Protection rman target / RMAN> set encryption on identified by ‘yourpassword’ only; You can backup with backup database command. Do…
How to Create Oracle Wallet for Encrpytion
Oracle Wallet Manager is a password protected stand-alone Java application tool used to maintain security credentials and store SSL related information such as authentication and signing credentials, private keys, certificates, and trusted certificates. 1- Create Wallet Directory [oracle@testdb ~] cd $ORACLE_HOME [oracle@testdb db_home] mkdir -p ORA_WALLETS 2- Write Wallet Location Information in sqlnet.ora File [oracle@testdb…
Disable root SSH Login on Linux Server
Root user is the most authoritative user on linux operating systems. You can take measure for security with disable root ssh. You can connect to server with other users. Edit sshd_config vi /etc/ssh/sshd_config #LoginGraceTime 2m #PermitRootLogin yes #StrictModes yes Note : “PermitRootLogin yes” is default value. This value allows ssh root login You have to…
Social Engineering Attacks
All social engineering techniques are based on specific attributes of human decision-making known as cognitive biases. These biases, sometimes called “bugs in the human hardware,” are exploited in various combinations to create attack techniques, some of which are listed here: Pretexting Pretexting is the act of creating and using an invented scenario (the pretext) to…
 Follow
Follow